If you have spun up an Azure DevOps Server in your environment or Azure DevOps Server Express installation, you will note that it defaults out of the installation with a port 80 configuration. It means your traffic is clear text over the wire. I will show you guys how to easily Install Self-Signed SSL Certificate in Azure DevOps Server and the steps required.
Generate a new self-signed certificate with PowerShell
As a note, a self-signed certificate is not for production environments, as you will want to make sure you have a trusted SSL certificate for security purposes in production. However, using a self-signed certificate in a home lab environment or other non-production environment is an easy way to secure communication over the wire with your Azure DevOps Server.
To easily spin up a self-signed certificate in Windows Server, we can use the new-selfsignedcertificate cmdlet.
The command to generate a new self-signed certificate for your Azure DevOps Server with PowerShell is the following. Just replace your “dnsname” with the name you want to use in your environment.
new-selfsignedcertificate -dnsname "azuredevops.cloud.local" -KeyLength 2048 -CertStoreLocation cert:\LocalMachine\My -NotAfter (Get-Date).AddYears(20)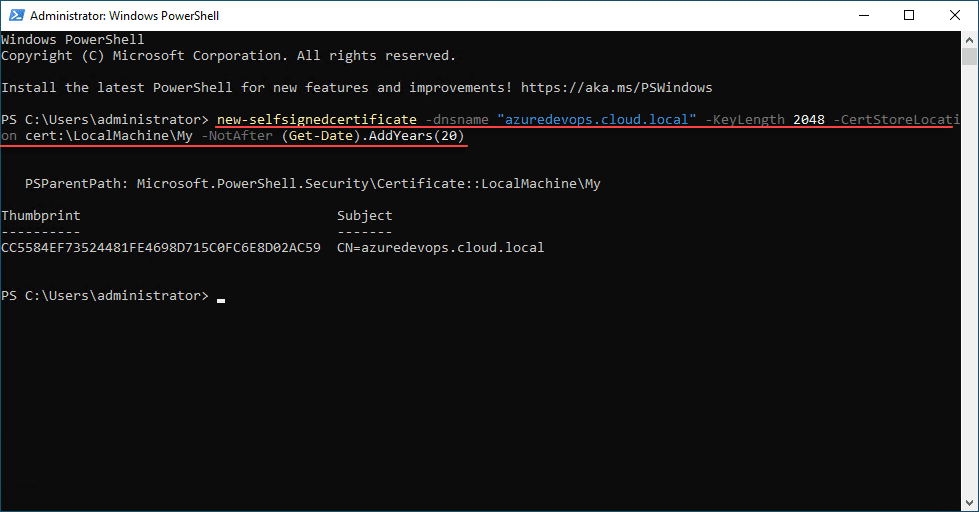
Edit the Azure DevOps Server IIS bindings
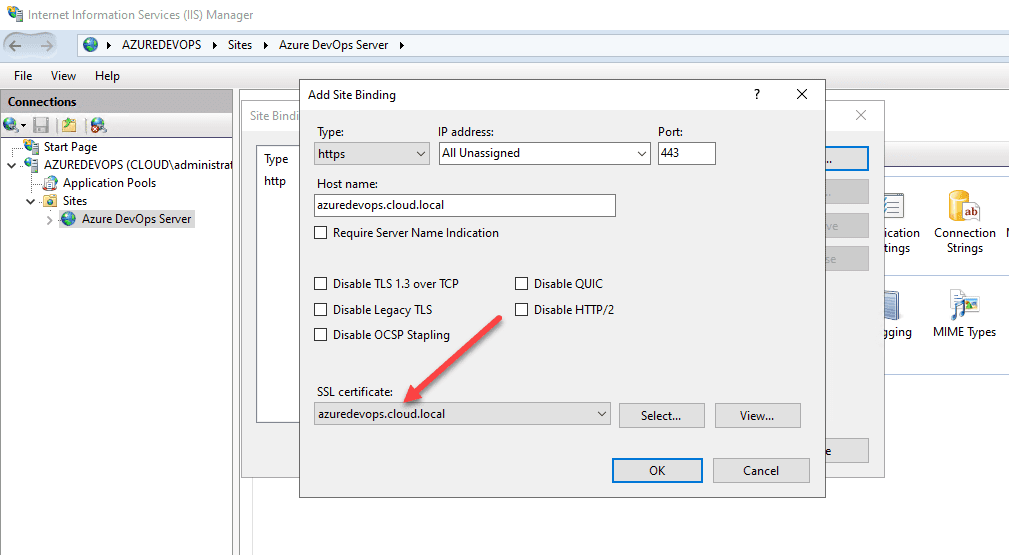
Now that we have a self-signed certificate with the subject name we want in our certificate store on the Azure DevOps Server, we can edit the bindings of the Azure DevOps Server in IIS. We will add a binding for SSL port 443.
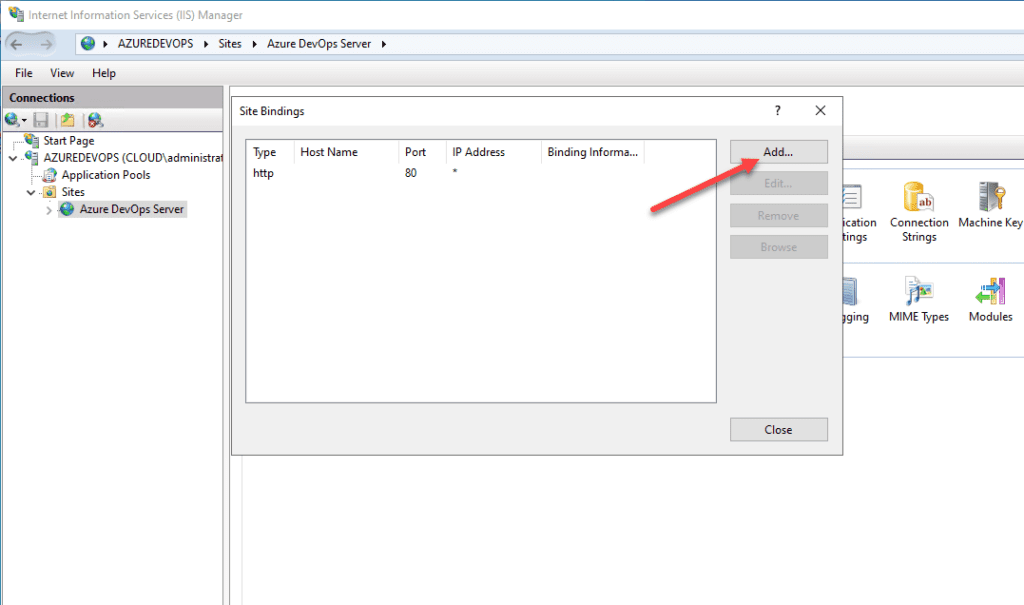
Add a new type of https and you can leave the IP address to All Unassigned. Make sure the port is 443. Then, populate your hostname. Make sure this matches what you used for the certificate. Under the SSL certificate, choose the self-signed certificate you created with the PowerShell command. Click OK.
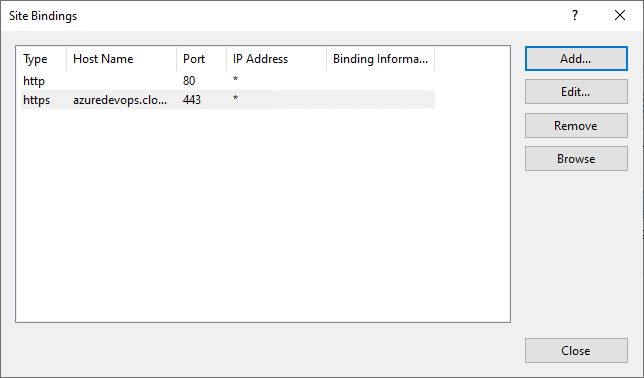
Now, we see the new SSL port 443 binding added for our Azure DevOps Server.
Changing the Azure DevOps Server configuration
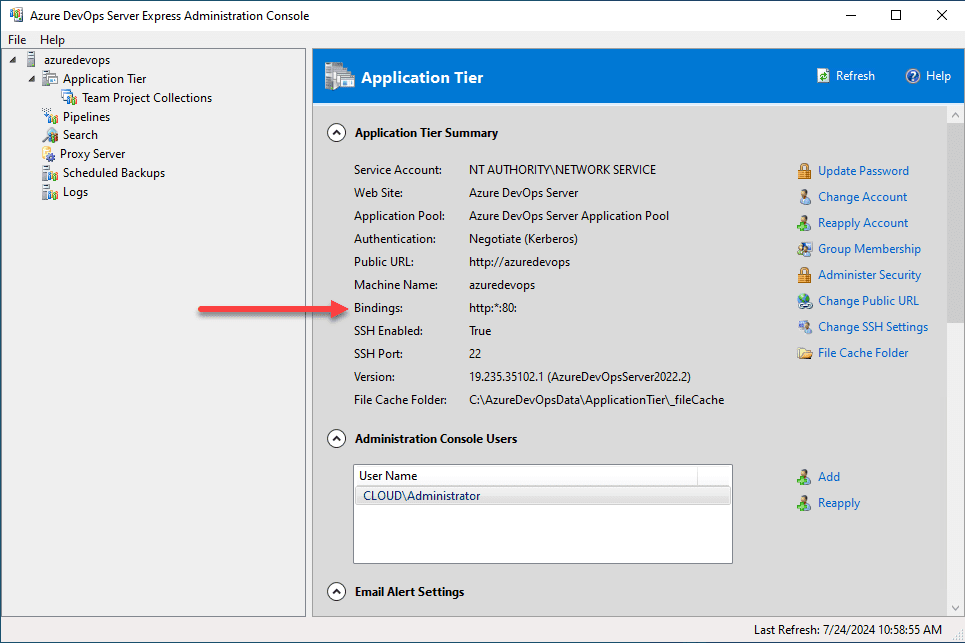
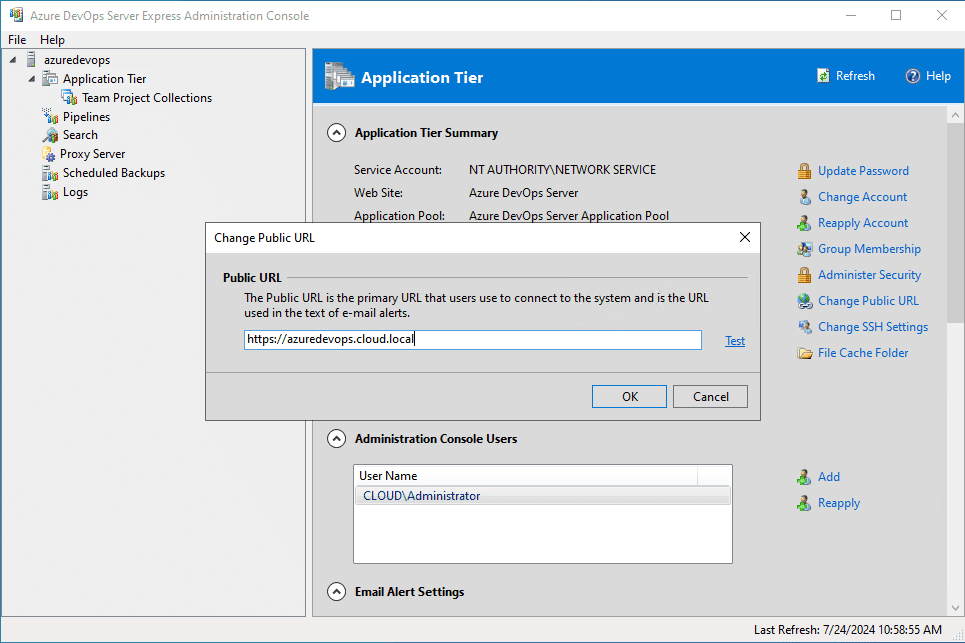
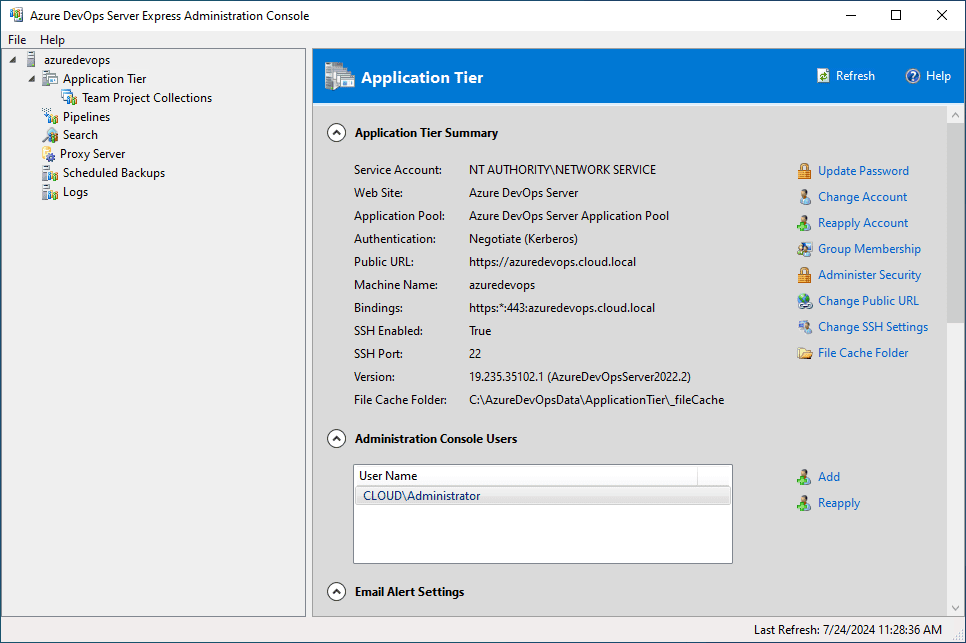
Now that we have the new certificate added as a binding in IIS, we need to go to our Azure DevOps Server configuration and change the default URL to point to the SSL binding. Click on your server in the Azure DevOps Server Express Administration Console. Then you will see the Bindings section. Click the Change Public URL link.
This will launch the Change Public URL dialog box. Enter the new https link for your Azure DevOps Server. As a note, with a self-signed certificate, if you choose to Test the URL, it will fail with “unable to verify the certificate.” This is expected since it is an untrusted self-signed certificate.
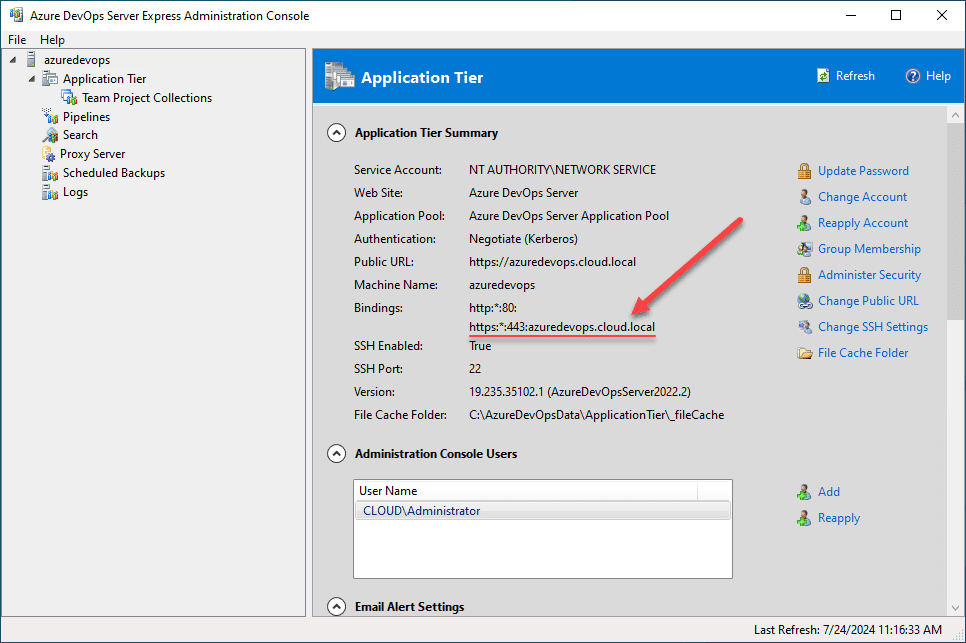
After adding the URL, we see the new SSL port 443 URL listed in the bindings section.
Browsing to the Azure DevOps Server website
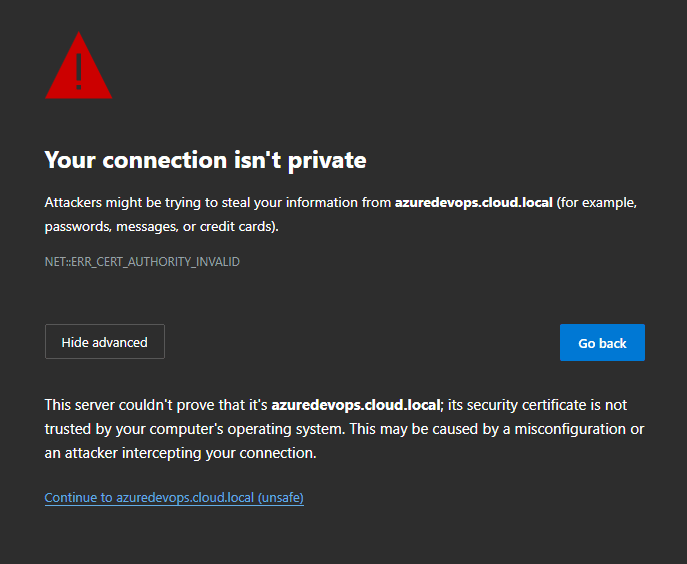
Now, we can browse to the URL. As expected, we get the SSL error for the URL.
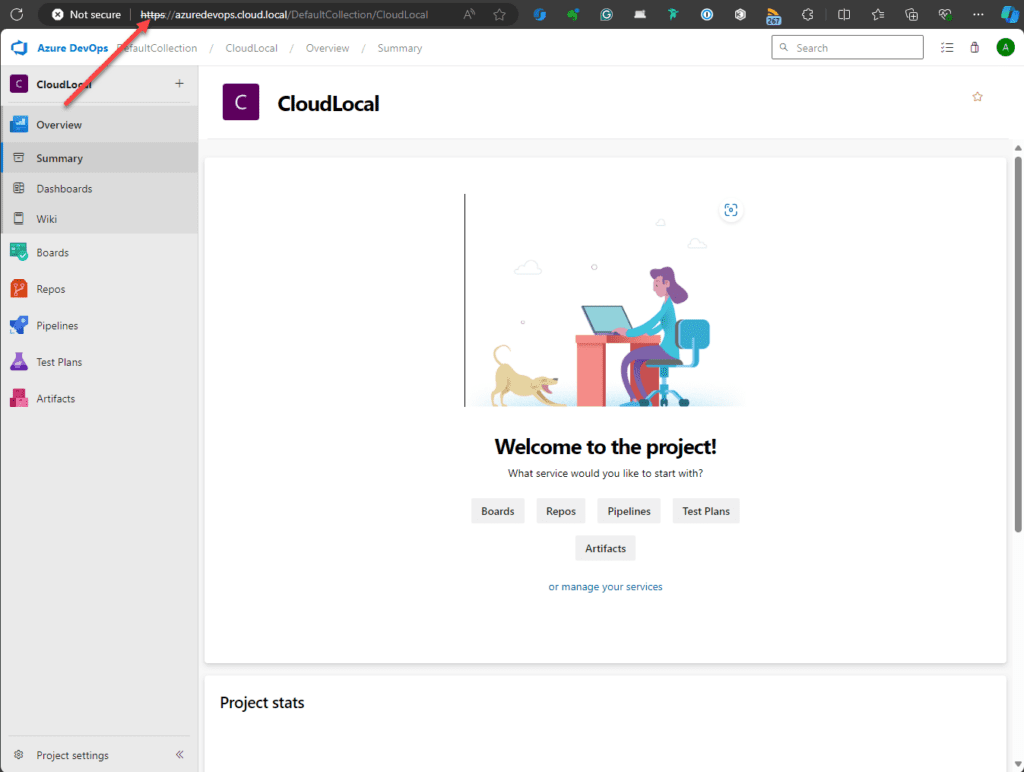
Removing the port 80 binding
Now that we have a certificate installed an the port 443 SSL binding in place in IIS and we have verified it is working, we can remove the port 80 binding. This is so no communication is possible over insecure port 80. Launch IIS manager (inetmgr.exe) and then edit the bindings on your Azure DevOps Server website.
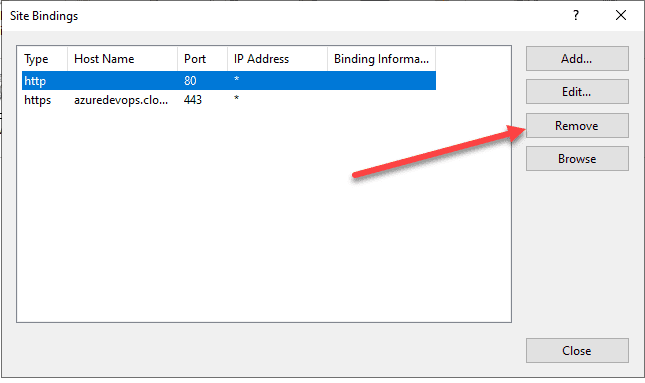
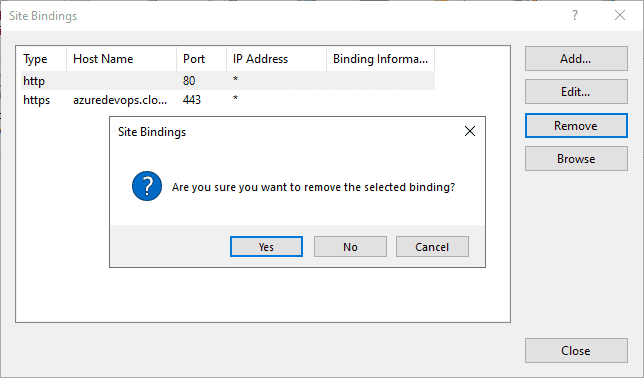
Click the port 80 binding, and then select Remove.
You will see the confirmation dialog box to remove the selected binding. Click Yes.
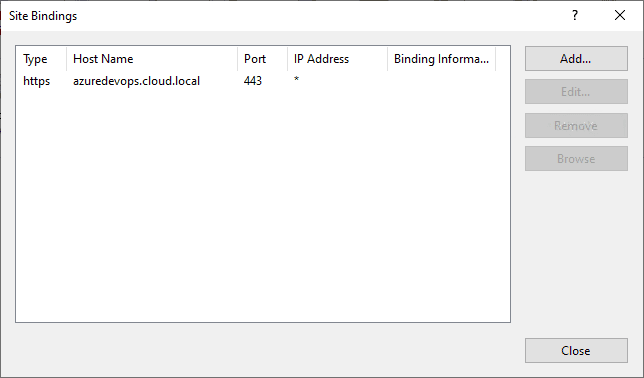
Now the port 80 binding will be removed and we will only see the port 443 SSL binding left.
After refreshing the configuration in the Azure DevOps Server Express Administration Console we only see the port 443 binding listed for the public URL.
Process is the same for a trusted certificate
As a note, the process we have gone through in this blog post is roughly the same as you would do if you installed a trusted certificate. You would need to create a certificate request (CSR), then get the trusted certificate back from your certificate authority. You would then add the binding as we have done here, selecting the trusted certificate, instead of the self-signed certificate.
Wrapping up
You can stand up an Azure DevOps Server Express installation in your home lab environment to start playing around with Azure DevOps and install self-signed SSL certificate in Azure DevOps Server to secure communication with your Azure DevOps Server so that communication doesn’t happen over clear text port 80.