In case you are running databases inside of AWS RDS, there is an upcoming change with the certificate used to secure the service in August 2024. There are actions that customers need to take now to make sure they are fully supported and don’t see any service disruptions with their database engine and client connections made from applications to RDS. Let’s talk about the AWS RDS-CA-2019 certificate expiring, why its happening, and what you need to do.
What is changing with AWS RDS and why?
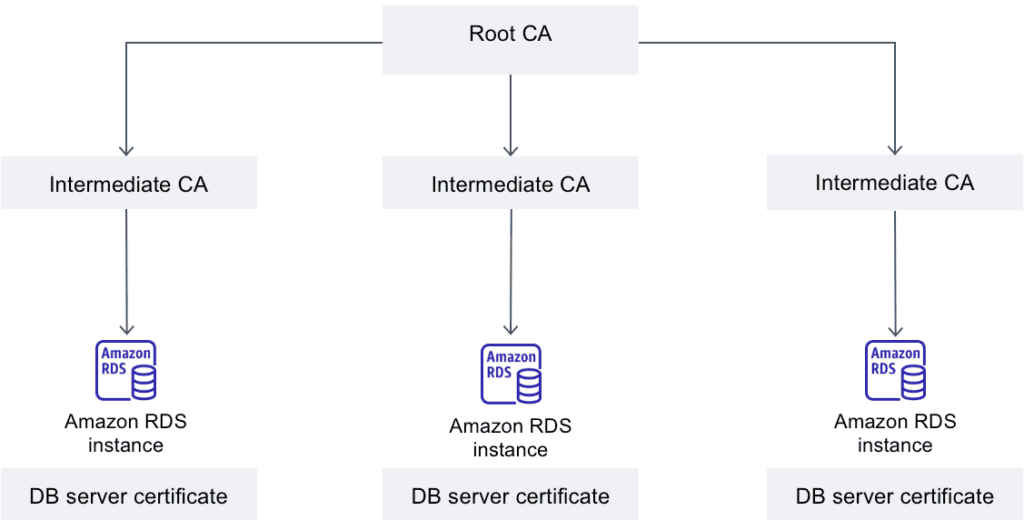
Amazon provides RDS certificate authority certificates to allow using SSL/TSL connections with certificate verification to AWS RDS databases or Multi-AZ DB clusters. As part of following their own best practices, Amazon RDS provides new CA certificates that are being rotated in, in place of the current rds-ca-2019 cert. So, the AWS RDS-CA-2019 Certificate expiring.
If customers currently do not use SSL/TLS connections with certificate verification to their database, they may still have expired CA certificates if they plan to use SSL/TLS in the future.
Take a look at the following high-level overview of AWS RDS certificate infrastructure, from their documentation here: Using SSL/TLS to encrypt a connection to a DB instance or cluster – Amazon Relational Database Service.
What new certs are being put in place?
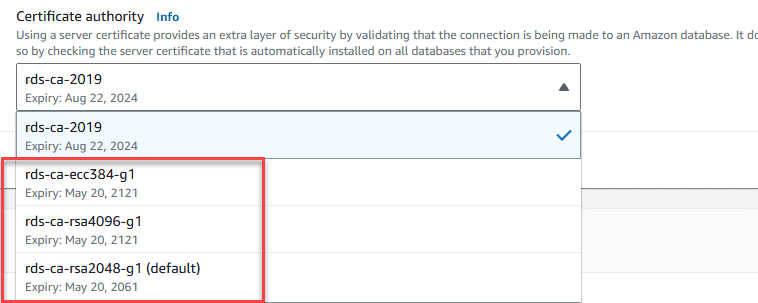
In December 2022, Amazon released new CA certs that will be valid for many years to come. So, hopefully, this will not be another issue that will affect most of us in our careers now :). Note the following new certificates and information:
- 40 years (
rds-ca-rsa2048-g1) - 100 years (
rds-ca-rsa4096-g1andrds-ca-ecc384-g1).
Further description of the certs:
- rds-ca-rsa2048-g1 – Uses a certificate authority with RSA 2048 private key algorithm and SHA256 signing algorithm in most AWS Regions. This CA remains valid for longer than the rds-ca-2019 CA. This CA supports automatic server certificate rotation.
- rds-ca-rsa4096-g1 – Uses a certificate authority with RSA 4096 private key algorithm and SHA384 signing algorithm. This CA supports automatic server certificate rotation.
- rds-ca-ecc384-g1 – Uses a certificate authority with ECC 384 private key algorithm and SHA384 signing algorithm. This CA supports automatic server certificate rotation.
So, this rotation of certs for RDS won’t happen for a very long time in the future, which is good to know.
Expiration timeline
What is the timeline for this expiration? Note the following table of information for timeline purposes on when AWS says the cert will be expiring and which regions will be affected when: Rotate Your SSL/TLS Certificates Now – Amazon RDS and Amazon Aurora Expire in 2024 | AWS News Blog.
| Expiration Date | Regions |
| May 8, 2024 | Middle East (Bahrain) |
| August 22, 2024 | US East (Ohio), US East (N. Virginia), US West (N. California), US West (Oregon), Asia Pacific (Mumbai), Asia Pacific (Osaka), Asia Pacific (Seoul), Asia Pacific (Singapore), Asia Pacific (Sydney), Asia Pacific (Tokyo), Canada (Central), Europe (Frankfurt), Europe (Ireland), Europe (London), Europe (Paris), Europe (Stockholm), and South America (São Paulo) |
| September 9, 2024 | China (Beijing), China (Ningxia) |
| October 26, 2024 | Africa (Cape Town) |
| October 28, 2024 | Europe (Milan) |
| Not affected until 2061 | Asia Pacific (Hong Kong), Asia Pacific (Hyderabad), Asia Pacific (Jakarta), Asia Pacific (Melbourne), Europe (Spain), Europe (Zurich), Israel (Tel Aviv), Middle East (UAE), AWS GovCloud (US-East), and AWS GovCloud (US-West) |
Checking your AWS RDS instance
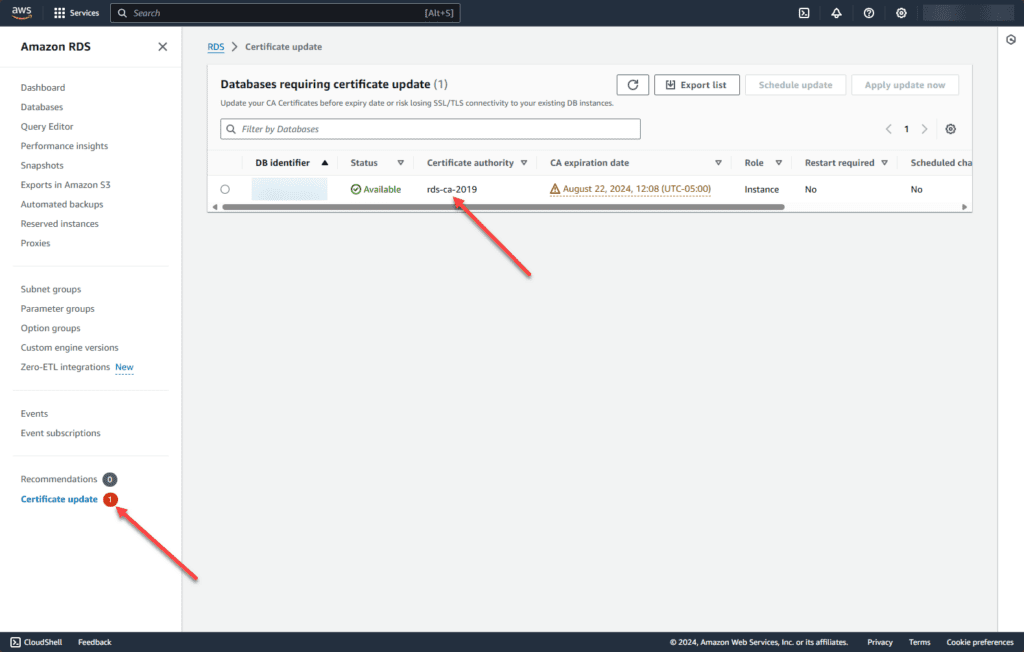
Navigate to your AWS RDS instance/region. You will see the following flags noted, including the Certificate update with a red indicator in the lower left-hand corner. You will also note the DB instance show the Certificate authority to be the rds-ca-2019 CA.
You can also use the AWS CLI command line to find instances with the affected CA:
aws rds describe-db-instances |
jq -r '.DBInstances[] |
select ((.CACertificateIdentifier != "rds-ca-rsa2048-g1") and
(.CACertificateIdentifier != "rds-ca-rsa4096-g1") and
(.CACertificateIdentifier != "rds-ca-ecc384-g1")) |
{DBInstanceIdentifier:
(.DBInstanceIdentifier), CACertificateIdentifier:
(.CACertificateIdentifier)}'What do you need to do before changing the cert?
While the process to change the certificate isn’t difficult, you need to update the trust store of any clients and applications that use the affected SSL/TLS cert. The heavy lifting with this operation will be making sure applications, source code, or configuration files being used will reference the new certificate and coordinate that change with your client applications.
Amazon makes mention, there is currently no easy way to see if your applications need certificate verification to connect.
Changing the cert on your AWS RDS instance
You shouldn’t change production first. Instead, you should use a test RDS instance that is non-production to test the change and ensure clients can connect with your applications using the new certificate.
Does the database need restarted for the certificate change?
To check if your database requires a restart to update the CA certificates:
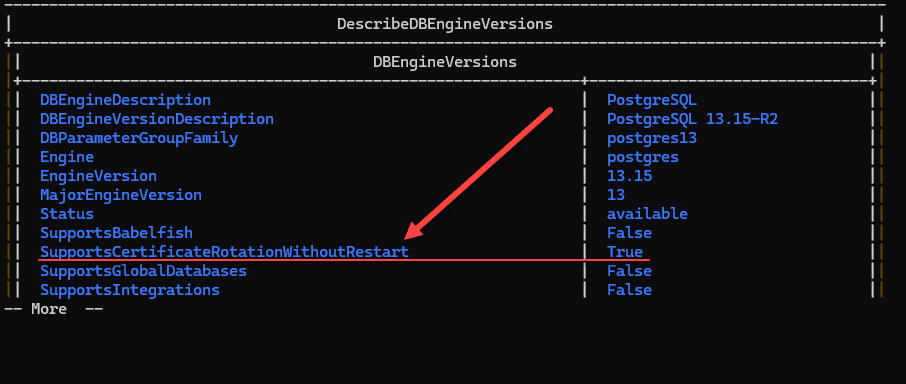
1) Use the describe-db-engine-versions command and check the SupportsCertificateRotationWithoutRestart flag.
2) You can go to certificate update tab and check the restart required column if it yes restart is required else no restart is required.
To easily check to see if a restart is needed for the certificate rotation, you can use the following AWS CLI command (example below checking PostgreSQL:
aws rds describe-db-engine-versions --engine postgres --output tableIt will return a table with configuration information and settings. We are interested in the SupportsCertificateRotationWithoutRestart flag. Here we see the DB indeed supports certificate rotation without needing a restart as it is set to True.
Wrapping up
Hopefully, this little PSA will help any who might not have noticed the expiration of the RDS certificate in their RDS instances. Thankfully, AWS RDS-CA-2019 certificate expiring is a fairly easy change on the AWS side. The major change will be changing this from a client application perspective if the older certificate is being used in the trust store for clients. Organizations will need to roll out the new cert before making the change on the RDS side of things.