If you work with many different types of Windows operating systems and you may still be supporting legacy applications that require downlevel versions of SSL and TLS, you have likely ran into the need to turn on deprecated SSL and TLS versions. If you have, and have hunted and search for the registry keys needed, etc, I want to introduce you to a tool that will make your life easier. Let’s look at the best SSL and TLS configuration tool for Windows.
Why do you need to change SSL and TLS configuration?
Well, that is a good question and in a perfect world, we don’t want to have to do that. In fact, Microsoft is doing a good thing by deprecating old or weak configuration settings and weak ciphers. However, unfortunately, many of us support applications or environments where legacy software and apps may still require old versions of SSL, TLS, and ciphers.
As an example, I recently had an issue with a developer where he was trying to connect a new Windows 11 VM he was running to an old SQL 2005 server (yeah I know SQL 2005, shaking head frustratingly). However, needs like this still exist.
Chasing down the registry keys needed to turn these settings back on can be frustrating as well. It can be confusing what you need to enable and which keys need to be added, etc.
Best SSL and TLS configuration tool for Windows
There is a GUI tool that makes life much much easier for admins and DevOps engineers alike. The tool is from a company called Nartac and is called IIS Crypto. You can download it here: Nartac Software – IIS Crypto.
You can download the IIS crypto GUI tool or the CLI. While the tool is developed for the use case of helping with enabling protocols and ciphers on web servers, it can also be used to configure SSL and TLS configurations on Windows clients as well and I have used it in this way many times. Whatever your need is, it will help either way.
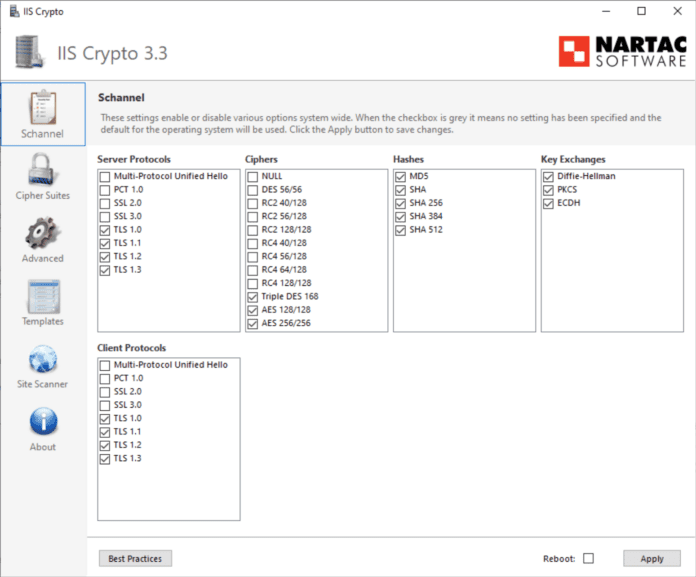
Here, I have downloaded the IIS Crypto tool. One thing I like about it is it is a self-contained executable. You just execute the .EXE and it won’t install anything, it will just run. Everything will look greyed out but you can click the protocols, ciphers, etc that you want.
And, best of all, you don’t have to edit the registry or get into the nitty gritty details of what you need to do to enable or disable protocols and ciphers.
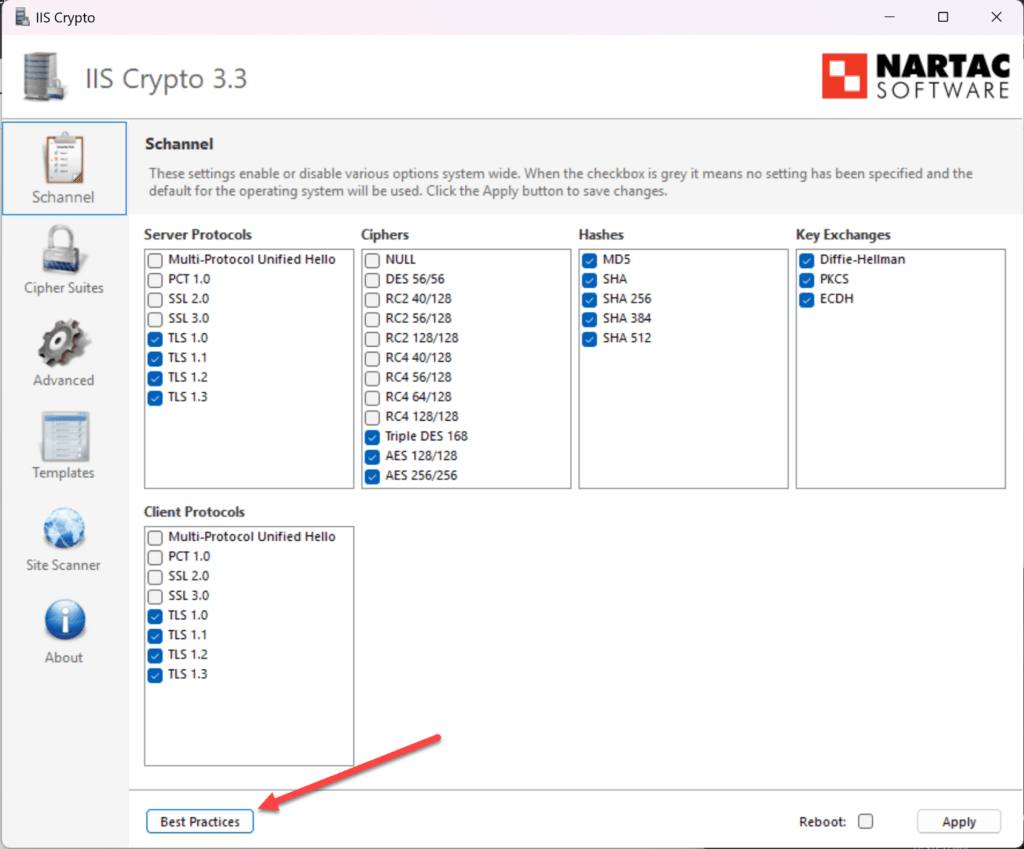
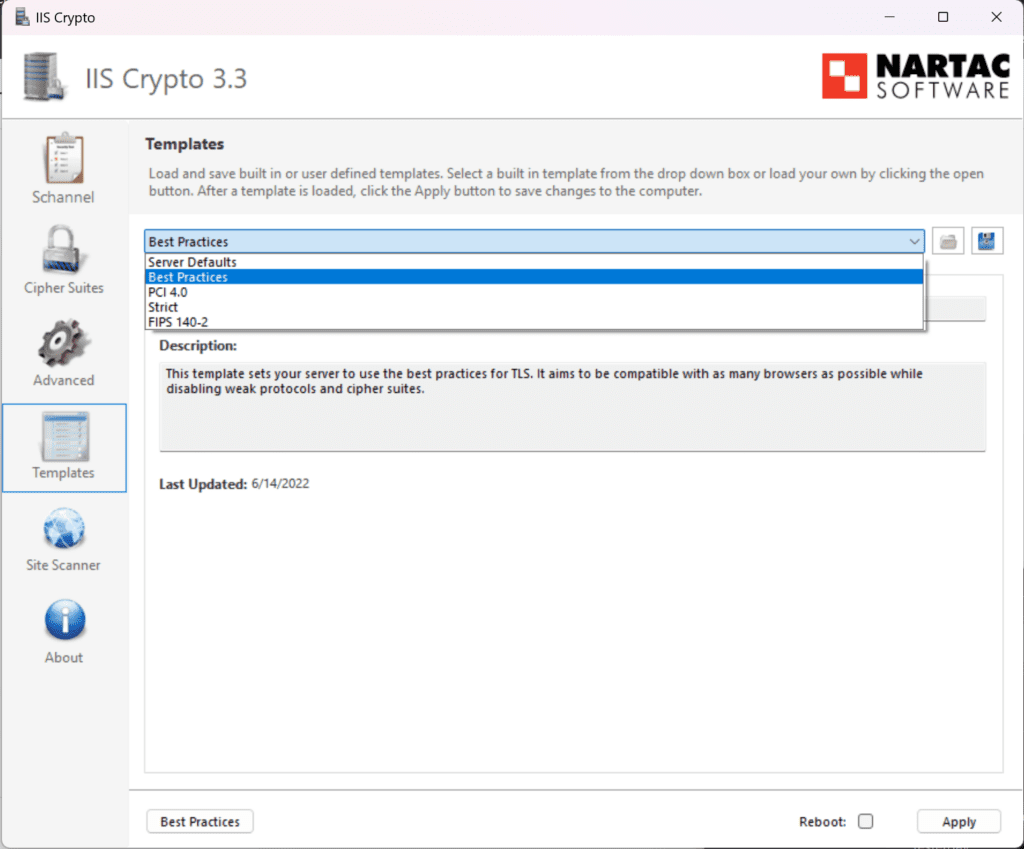
One feature I really like about the program is that it has a best practices button that allows you with a single click of a button to enable the recommended protocols and ciphers based on security recommendations. As we will see below, the template that it works from is configurable.
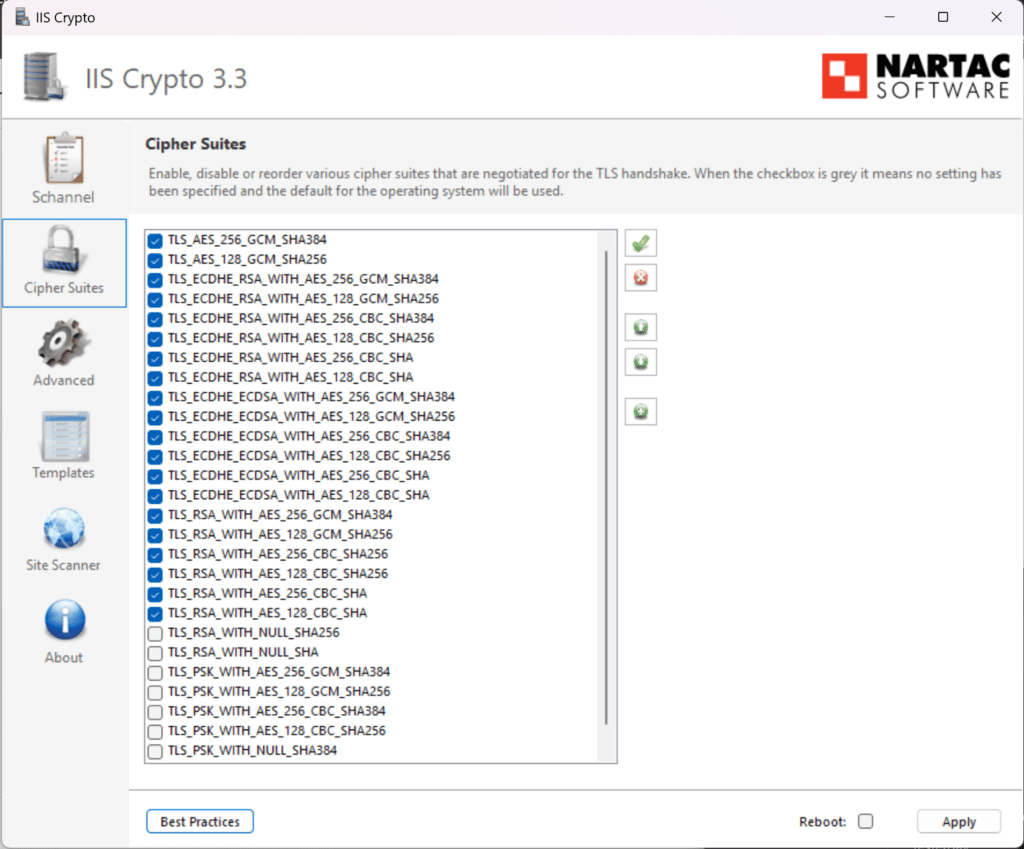
When you click the Cipher Suites, you will see the Ciphers listed that are configurable and you can simply click the ones you want.
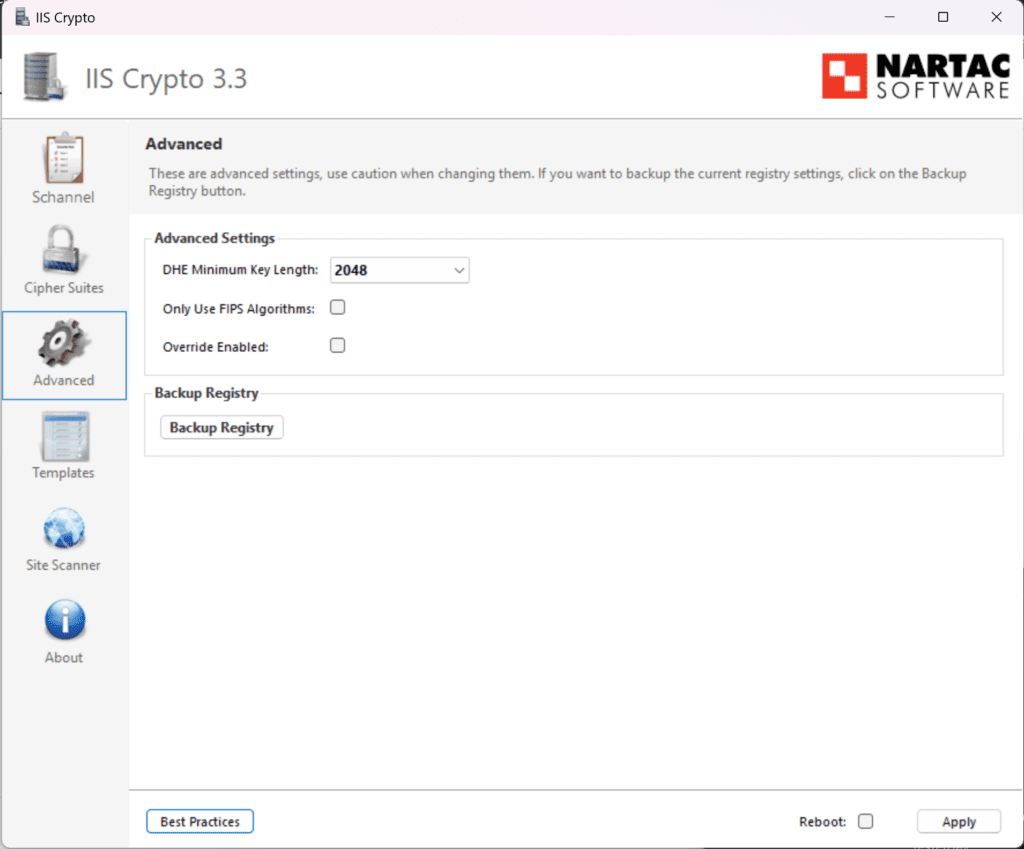
If you click the Advanced button, you will see advanced settings like DHC Minimum Key length, FIPs algorithm settings, etc.
When you click Templates, you will see where you can configure the best practices template that is used to show you the recommended protocols and cipher suites.
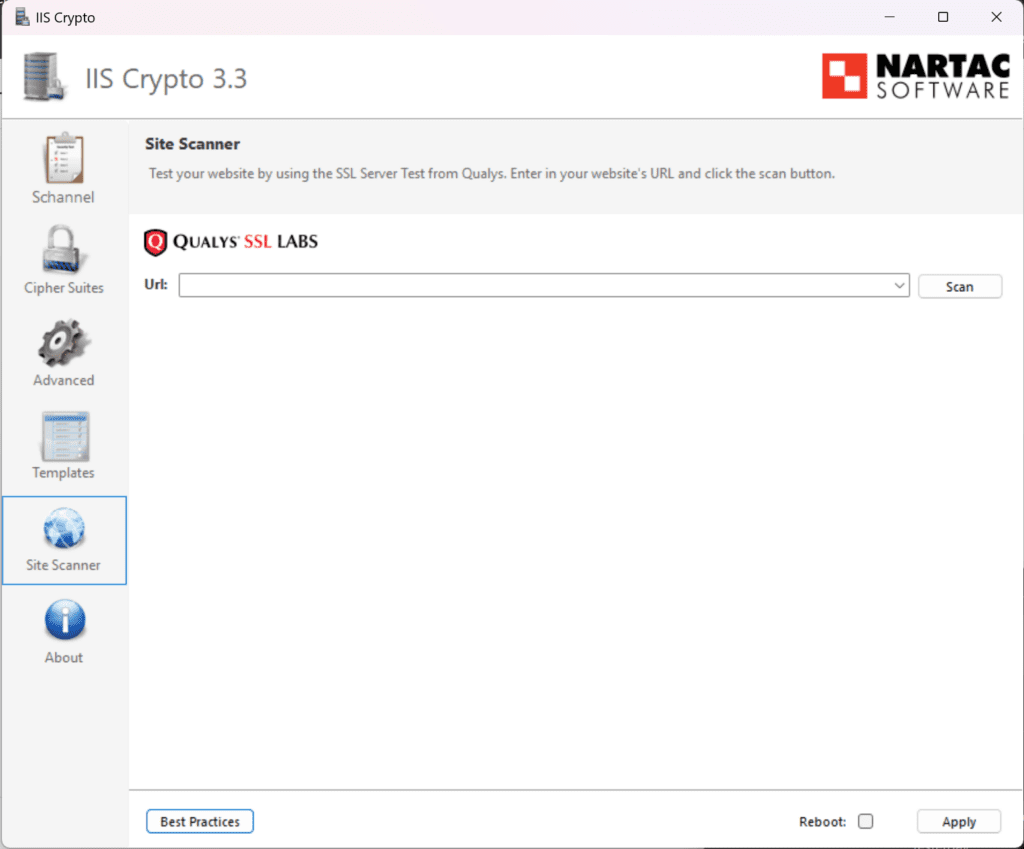
Site scanner found in the IIS Crypto tool lets you scan a website/webserver to see which protocols and ciphers are allowed to see if these are set to best practices.
Make SSL and TLS changes cautiously
While taking away weaker and older protocols and ciphers may at worst cause certain clients or apps to stop working, adding old or weak SSL and TLS protocols and ciphers can give attackers what they need to compromise your web server or your network. So, make changes, especially those that add old or weak technologies very carefully and only really as a last resort to satisfy a necessary configuration.
Wrapping up
While you can hack at the registry and look up the keys you need to add to reenable old or weak protocols, using the Nartac IISCrypto tool is a much easier and better way to do this since it eliminates the possibility of mistyping registry keys or doing something in the registry you shouldn’t do. While the tool is meant to be used for checking, enabling, and disabling protocols and ciphers on a web server, it can also be used for clients to configure their SSL and TLS protocols and cipher